As businesses and individuals increasingly migrate to cloud environments, the need for robust cloud security services has never been more critical. Cloud technology has revolutionized the way data is stored, processed, and accessed, but with these advantages come new challenges in ensuring the security and privacy of sensitive information. This article explores the significance of cloud security services in the United States, highlighting how these services play a pivotal role in safeguarding data across the nation.
- Securing the Foundation of Digital Transformation: Cloud security services form the bedrock of the digital transformation sweeping across America. As organizations embrace cloud technology to enhance efficiency and scalability, these services ensure that the foundation of this transformation is fortified against potential cyber threats.
- Data Encryption in Transit and at Rest: U.S. cloud security services prioritize data encryption to protect information both in transit and at rest. Advanced encryption algorithms safeguard sensitive data as it travels between users and cloud servers, as well as when it resides within cloud storage, ensuring confidentiality and integrity.
- Identity and Access Management (IAM): IAM solutions are integral to cloud security in the U.S., providing robust access controls that govern user permissions and authentication. This ensures that only authorized individuals can access specific data and functionalities within the cloud environment, minimizing the risk of unauthorized access.
- Multi-Factor Authentication (MFA): Enhancing user authentication, U.S. cloud security services often incorporate multi-factor authentication. By requiring users to provide multiple forms of identification, such as passwords, biometrics, or authentication tokens, these services add an extra layer of security to prevent unauthorized access.
- Threat Intelligence and Detection: Cloud security services in the United States leverage advanced threat intelligence and detection mechanisms. By continuously monitoring for suspicious activities and potential security threats, these services enable rapid identification and response to security incidents, ensuring a proactive defense posture.
- Secure APIs and Integration: APIs (Application Programming Interfaces) are crucial for the seamless integration of cloud services. U.S. cloud security services focus on securing APIs to prevent vulnerabilities that could be exploited by cybercriminals, ensuring the safe exchange of data between cloud applications.
- Regular Security Audits and Compliance: To uphold the highest standards of security, U.S. cloud security services conduct regular security audits and ensure compliance with industry and regulatory standards. This proactive approach helps organizations maintain a secure and compliant cloud environment.
- Incident Response and Recovery: Acknowledging the inevitability of security incidents, cloud security services in the U.S. include robust incident response and recovery mechanisms. This enables organizations to swiftly respond to security breaches, mitigate potential damage, and recover operations with minimal downtime.
- Continuous Monitoring and Automated Security Updates: Continuous monitoring is a key aspect of cloud security services, with automated systems providing real-time insights into the security status of cloud environments. Automatic security updates ensure that cloud services are equipped with the latest protections against emerging threats.
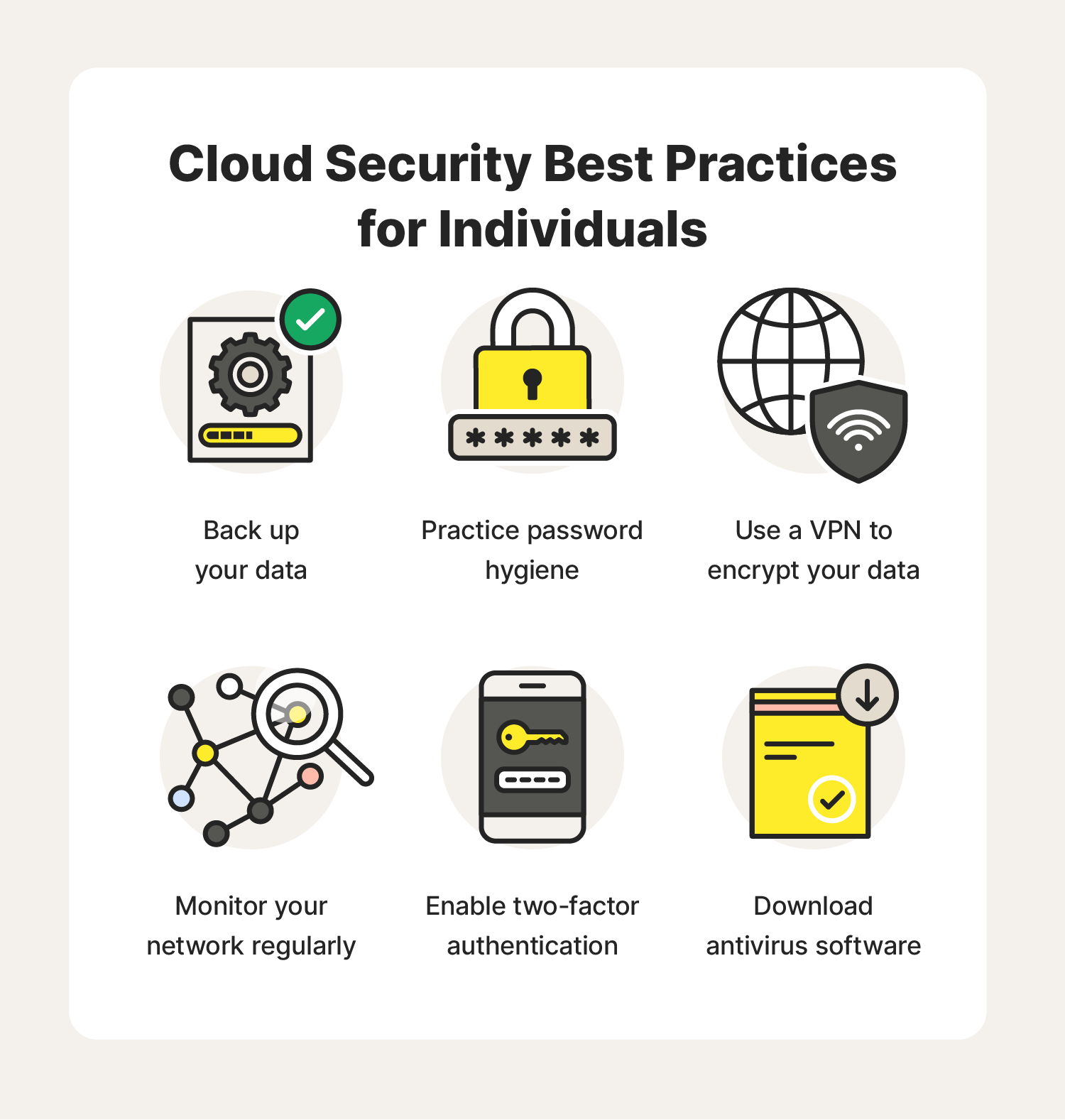
- Educating Users on Cloud Security Best Practices: Beyond technical measures, U.S. cloud security services often include educational components to promote user awareness and best practices. Training programs help users understand their role in maintaining a secure cloud environment, fostering a culture of cybersecurity.
Conclusion:
Cloud security services are instrumental in safeguarding the data that fuels the digital landscape of America. By incorporating cutting-edge technologies, robust access controls, and a commitment to proactive defense, these services ensure that businesses and individuals can embrace the benefits of cloud technology with confidence, knowing that their data is secure across the vast expanse of the cloud.

